
Real vs Fake Tech Products: Shocking Truths You’ll Love (and Fear)
(Read This First 👀) What if a $80 “fake” speaker sounded better than a $300 original? And what if a $300 phone looked perfect… but collapsed the moment you actually…
Read more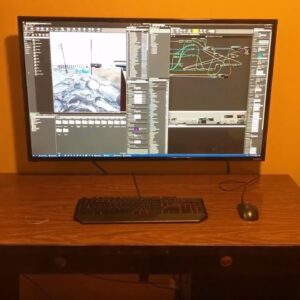
Use TV as Computer Monitor: The Smart (and Risky) Truth
Ever looked at your small laptop screen and thought, “Why am I squinting when a giant TV is right there?” Good news: you can use a TV as a computer…
Read more
Future of Remote Work Technology: High-Performance Tools to Monitor, Secure & Pay Global Teams
Remote work isn’t a trend anymore — it’s the new normal. As companies build global teams, leaders face three big challenges: How do you monitor remote employee productivity without destroying…
Read more
AI-Powered Cyber Defense: Stopping Real-Time Attacks in 2026
The cybersecurity landscape has reached a point of no return. As we move through 2026, the traditional “firewall and antivirus” approach is as obsolete as a dial-up modem. Today, hackers…
Read more
Big Data for Business: How to Predict Sales & Dominate 2026
The era of “gut feeling” entrepreneurship is over. In 2026, the world’s most successful business owners aren’t just working harder; they are working smarter by turning raw information into a…
Read more
IT Compliance 2026: Avoid Fines with Automation Tools
The regulatory landscape has officially entered “Hyper-Drive” mode. In 2026, the cost of being “late” to a compliance update is no longer just a slap on the wrist—it’s a financial…
Read more
How Businesses Use Big Data Analytics to Predict Customer Behavior and Increase Profits by 300%
Big data analytics has moved from a buzzword to a profit-driving engine for modern businesses. Today, companies that understand customer data, predictive analytics, and AI-driven insights consistently outperform competitors that…
Read more
Remote Tech Careers 2026: Skills for Global High-Pay Jobs
The global workforce has undergone a seismic shift. As we navigate 2026, the dream of earning a Silicon Valley salary while living in a completely different time zone is no…
Read more
Zero Trust Security: The Tech Shielding Banks and Governments in 2026
The “castle-and-moat” era of cybersecurity is officially dead. In 2026, hackers no longer “break in”—they “log in.” As digital threats evolve into hyper-intelligent, AI-driven entities, traditional firewalls are as effective…
Read more
High-Paying Remote Tech Jobs: Your 2026 Career Roadmap
The “Great Remote Migration” has reached its peak. In 2026, working from a home office in Lagos, a beach in Bali, or a flat in London for a Silicon Valley…
Read more