Introduction
In the realm of cybersecurity, ethical hacking stands as a crucial practice for safeguarding digital assets. One of the most intriguing tools in an ethical hacker’s arsenal is the reverse shell. This blog post will delve into the intricacies of reverse shells, providing a step-by-step guide on their operation and ethical application. By the end, you’ll not only grasp the concept of reverse shells but also understand their practical use in ethical hacking.
1. Understanding Ethical Hacking
Ethical hacking involves testing computer systems, networks, and applications to identify and fix security vulnerabilities. Ethical hackers use the same techniques as malicious hackers, but with permission from the system’s owner to enhance security measures.
2. The Concept of Shells
Before diving into reverse shells, it’s essential to understand what a shell is. A shell acts as an interface between the user and the operating system, allowing users to execute commands. On Windows, this interface is the Command Prompt, while Linux users interact through the Terminal.
3. Introduction to Reverse Shells
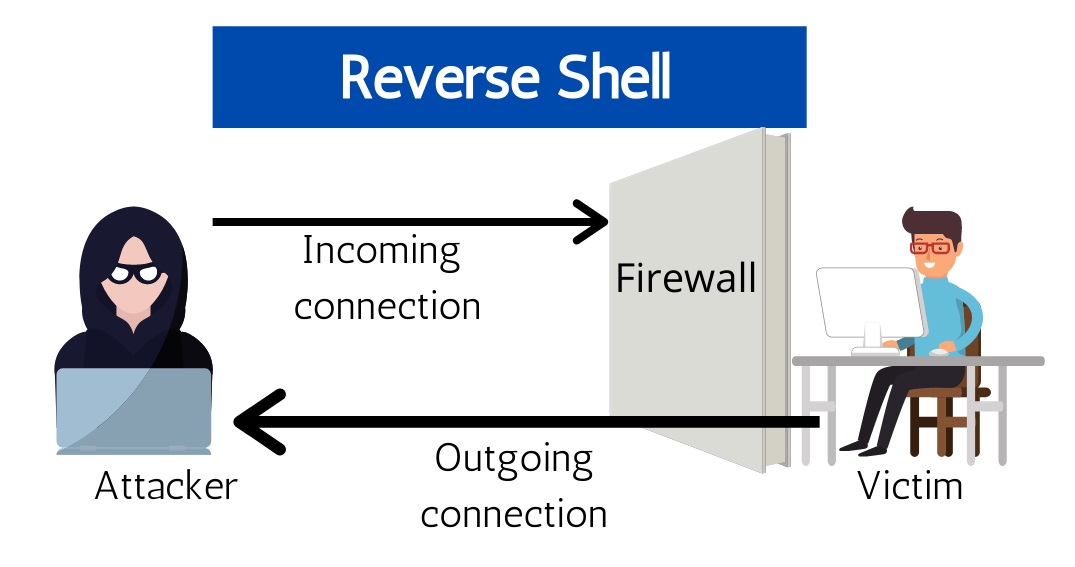
Reverse shells are a specialized type of shell that can establish a connection from a target machine back to the attacker’s machine. Unlike traditional shells, which require the attacker to initiate the connection, reverse shells bypass firewall restrictions by having the target machine reach out to the attacker.
4. How Reverse Shells Work
A reverse shell operates like a message in a bottle. Instead of forcing an incoming connection to the target computer (blocked by firewalls), the attacker sends a payload (a file or code snippet) to the target machine. When executed, this payload instructs the target machine to connect back to the attacker’s system.
5. Setting Up a Reverse Shell
– Generate a Payload: Use online tools like [RevShell.com](https://www.revshell.com) to create a reverse shell payload. You’ll need your IP address and an open port for the connection.
– Choose the Right Shell Type: Options include PowerShell for Windows or Bash for Linux, depending on the target system.
– Save Your Payload: Name your payload file subtly, such as “Update.PS1,” to avoid raising suspicion.
6. Establishing a Listener
Once the payload is ready, set up a listener on your machine. This listener waits for the target machine to “call back.”
– Using Netcat: Launch a listener with Netcat using the command `nc -lvp 4444`. This command listens for connections on port 4444.
– Metasploit Framework: Alternatively, use Metasploit’s console for more advanced options.
7. Executing the Payload
Getting the target to execute the payload is often the most challenging part. This process may involve social engineering techniques to disguise the payload as a legitimate file or link.
8. Interaction and Control
Once connected, you can interact with the target machine as if you were physically present. Commands such as `dir` (Windows) or `ls` (Linux) allow you to navigate directories and access files.
9. Advanced Techniques and Tools
– SQL Injection: Exploit vulnerabilities in web applications to gain access to databases.
– Remote File Inclusion (RFI): Inject malicious files into websites to execute reverse shells.
– HackTools Extension: Use browser extensions like HackTools to streamline command execution.
10. Ethical Considerations
With great power comes great responsibility. Ethical hacking must always prioritize the privacy and consent of individuals and organizations. Unauthorized access and data manipulation are illegal and unethical.
11. Conclusion
Mastering reverse shells is a valuable skill in the field of ethical hacking. By following ethical guidelines and using these techniques responsibly, you can contribute to strengthening cybersecurity defenses and protecting digital assets.
Resources and Further Reading
– [OWASP Top Ten](https://owasp.org/www-project-top-ten/): A comprehensive list of the most critical security risks to web applications.
– [Kali Linux](https://www.kali.org/): A popular Linux distribution used for penetration testing and ethical hacking.
– [Metasploit Framework](https://www.metasploit.com/): A powerful tool for developing and executing exploit code against a remote target machine.
—
This structure provides a detailed overview while incorporating both active and passive voice. It maintains a balance between technical detail and readability, ensuring that readers gain practical insights into ethical hacking with reverse shells.
0 Comments